The Anatomy of a 'Denial of Service' Attack
Written on March 15, 2000 by Robert & Karen Vanderzweerde
Appeared in Greenmaster Magazine
If you tried to access Yahoo!, Amazon.com, E*Trade, Buy.com, eBay, ZDNet, or
CNN during the first week of February on the world wide web, you might have
experienced the 'world wide wait'. Even HMV in Canada was affected. But wait
(sic) … this delay was not caused by thousands of users, poor site design, or
inadequate network or computing capacity -- the usual causes of slow response.
These sites are well designed and readily able to process the high demands put
upon them by their visitors and customers.
So what happened?
This delay was caused deliberately and maliciously. Called a 'denial of
service' or 'flood', torrents of bogus requests were sent to each site. We're
not talking about a doubling or tripling of network traffic … Yahoo! received
millions of messages every hour (most companies dream of receiving this much
usage in a year, let alone each and every hour). While each site tried to
process or even discard the junk being sent its way, normal users of the site
were effectively blocked from accessing the site … hence the name, 'denial of
service'.
How did they do that?
Now, you can't just use your average personal computer to create this kind of
bogus traffic. For one thing, you just can't type fast enough to flood one of
the major sites -- they expect thousands of people to use their site every
minute. Also, the requests you make could be traced back to you and you will be
caught. So how did these people, known as 'crackers' or 'hackers', do it and get
away with it?
To create a 'flood', tens or hundreds of computer need to be used (i.e. many
small hoses coordinated to fill a very large pipe) but this is expensive. Where
did the cracker get the money? Believe it or not, there is software freely
available on the world wide web to create world wide waits. Anyone with some
computer experience can download and implement this software. The commonly
available ones are Tribal Flood Network (TFN), trin00, and stacheldraht (German
for barbed wire).
To implement an attack, the cracker uses well-known security holes to break
into other computer systems or servers and installs a small piece of software.
This is known as a Trojan Horse as it is later triggered by the cracker to do
its dirty deeds (as opposed to a Virus on an computer which is triggered by an
event such as a date). When the cracker has installed enough Trojan Horses, they
initiate the 'flood' by telling all the Trojan Horses to simultaneously send
bogus messages at the specified target site. The administrators of the computers
running the Trojan Horses don't even know that they have been conscripted as
part of the attack force. The target site may not even know that an attack is
taking place until someone complains of slow service.
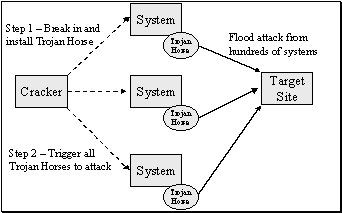
Figure 1 - Anatomy of a Flood Attack
The target site must act quickly to stop the attack, often by shutting down
their servers and switching over to backup systems.
How do you prevent an attack?
While denial of service attacks are not new, the presence of Tribal Flood
Network, trin00, and stacheldraht were detected and alerts were issued in 1999.
All administrators were urged to see if Trojan Horses had been installed on
their systems without their knowledge. There is even free software available
that could scan systems and report if the Trojan Horses are present (much like a
Virus scan). But, like the rest of us, these administrators are pressed for time
and many of them have not yet scanned their systems.
Detecting and blocking an attack is difficult. At best, an early response can
be initiated rather than waiting for a customer to complain about slow service.
To respond, simply blocking the bogus traffic is not enough -- the traffic must
be examined to see if it is bogus but by that time, the network link is already
flooded. While there isn't much to actually prevent an attack, the effects can
be lessened. For example, network links can be made very large to make it
difficult to flood (this is why an attack on AOL was ineffective).
More attacks are certainly possible and probable in the future. 'Floods' are
annoying to people trying to legitimately use a site and damaging to companies
because of lost revenues and bad publicity. The good news is that information on
the sites under attack remains secure. The integrity of these sites and any
order/payment information was not compromised. Nevertheless, you should always
be careful about proving credit card and other key information about yourself
over the web.
|