Can You be Scanned or Cracked?
Written on June 27, 2000 by Robert & Karen Vanderzweerde
Appeared in Greenmaster Magazine
It's a scary digital world we live in with viruses like ILOVEYOU, denial of
service attacks on major web sites, junk e-mail (also known as 'spam'),
questionable uses of private information, and computer crackers who break into
systems. Crackers may steal information like credit card numbers, modify web
sites, and cause other mischief.
Many people don't give out even a smidgen of information to anyone on the
Internet, delete junk mail without opening it, run virus scans and backups
regularly, disable browser cookies, and regularly change their well thought out
passwords. They are confident that they are safe and secure.
Well, that may not necessarily be true. Every time you connect to the
Internet, you are potentially exposing the entire contents of your computer for
everyone on the web to scan, copy, or destroy. People with persistent or
broadband connections (e.g. cable modems) are more vulnerable but those that use
a dial-up connection are at risk too.
How can they do this?
Every time you connect to the Internet, you are assigned an IP address. This
IP address allows you to communicate to other parts of the web (e.g. surfing to
sites or downloading e-mail). You send out a request (e.g. type in a web site
address) and your message goes to that server to fetch information. You IP
address tells the server where to send the response. Without an IP address, no
communication can occur.
The problem is that web traffic is two-way. Someone could send a request to
your computer (e.g. copy all the files) and, unless you are protected, your
computer will answer.
How is that possible?
There are several user-friendly features in Windows that make the computer
easy for you to use without a lot of technical knowledge but inadvertently
expose your computer.
For example, when you installed your modem and a connection to your Internet
Service Provider (ISP), Windows "bound" that information into its
network configuration. Since most people don't even know what binding is,
Windows "binds" the information in the most promiscuous manner so that
the feature you are likely to want is enabled (see Figure 1).
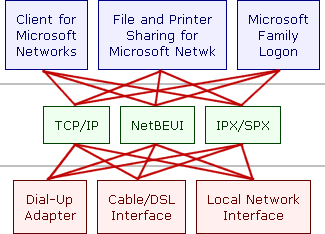
Figure 1 - Promiscuous Bindings
As you can see, the diagram doesn't make much sense unless you have a lot of
computer knowledge. The flaw in being overly connected is that if you turn on
"File and Print Sharing" on your computer, you will share your files
directly to the Internet as well and anyone can copy them.
How can I protect my self?
The easiest thing to do is to turn off "File and Print Sharing".
This can be found in the Network icon in the Control Panel. Double click on it
to open it and then click on the "File and Print Sharing" button. The
settings should look like Figure 2. If not, simply click on the checkmarks to
remove them and then click on OK.
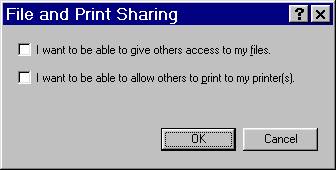
Figure 2 - File and Print Sharing
Note that password protecting your files is not sufficient if you have
"File and Print Sharing" enabled and you are logged onto the Internet.
I've seen password crackers decode passwords using common words, names, and
places in two seconds. There is also another flaw in Windows where password
attempts are unlimited and not logged (i.e. someone can try a million passwords
on your computer and you won't even know it). It is better to disable "File
and Print Sharing".
But they'll never find me.
Oh yes they will!
Internet hackers and crackers seem to have hours of time to hunt you down and
get access to your information. In fact, there are automated scanning tools that
try all IP addresses (yours included) and scan your ports for vulnerabilities.
Someone could scan millions of IP addresses every hour without breaking a sweat.
With "File and Print Sharing" disabled, they can find you but will
not be able to get in. To test yourself, there is a site that will scan your
computer for free at http://grc.com and click on Shields Up! to get to the test
programs. The message that indicates you are safe is "Unable to connect
with NetBIOS to your computer".
If you are really concerned, there are products, known as firewalls, that you
can install on your computer that will prevent access (even if you have
"File and Print Sharing" enabled). Some of the more popular and proven
products include:
- Norton's Internet Security 2000
- Black ICE Defender
- McAfee's ConSeal Private Desktop
- Zone Alarm (free too!)
|